THANK YOU FOR SUBSCRIBING

Securing Telco Cloud for the 5G Era
Srinivas Bhattiprolu, Head of Advanced Consulting Service, Nokia Software


Srinivas Bhattiprolu, Head of Advanced Consulting Service, Nokia Software
Cloudification of Communications Service Provider (CSP) network is imminent
The concept of cloud has become ubiquitous and has made inroads into the networks of communications service providers (CSPs). 5G will create new cloud-based applications and opportunities that are unviable with current network blueprints. CSPs in the past have always questioned migrating the network functions in their entirety to a public cloud as they are often skeptical of its security; however, no CSP can discount that hybrid cloud strategy will be a cornerstone for their 5G plans.
In the 5G realm, it is important to remember that networks will become programmable, so the power of the cloud will be needed to future-proof the network and drive the costs down, taking advantage of economies of scale. This is the only way CSPs can exploit the 5G metamorphosis - by embracing a holistic and secure hybrid cloud strategy.
The Telco Cloud
The telco cloud is based on the predominant idea of codifying network elements of CSPs to create an ameliorated experience and scalability. Currently, the network functions are an integration of hardware, software, applications, and data. This approach is resource-intensive and not scalable for the new digital world. This is now creating a scenario where legacy orchestration solutions are separated from the digital infrastructure vis-a-vis the cloud, virtualization, and containers.
An effective integration of these domains (orchestration and infrastructure) is possible through the telco cloud. Open-source platforms are gaining popularity in these two worlds. These platforms will help bring down the Total Cost of Ownership but will add additional complexities. Many CSPs are already contemplating a unified digital infrastructure across network functions and IT applications to exploit the above-mentioned levers.
What are the possible vulnerabilities and threat vectors in a telco cloud?
Telco cloud environment will be intricate and heterogeneous, including multiple tiers, technologies, deployment models, applications/network functions, and APIs. The diversity of cloud computing models poses a security risk where different types of attacks are now targeting the cloud infrastructure. Static, manual, and perimeter security are obsolete and ineffective for dynamic clouds. Security breaches will have serious ramifications for CEOs and other key stakeholders. The threat vectors are ever-expanding. Prevention is more desirable than a cure, and implementing proactive security measures will go a long way in protecting the crown jewels for CSPs.
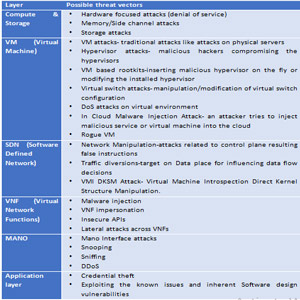
An end-to-end telco cloud system encompasses multiple components, each of which can be subjected to distinctive attacks. An illustrative view of the cloud infrastructure threat landscape is depicted below:
There are myriad threat vectors, and attacks can ensue with or without any human involvement.
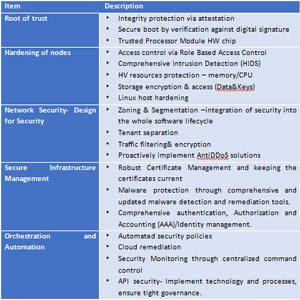
A few best practices
The threats and vulnerabilities are different, so there is no silver bullet for securing a telco cloud. A few best practices will aid in this process, some of them are depicted below. CSPs must embrace the agility and innovations associated with the Internet world. Moving toward, a zero-touch architecture with extreme automation is essential to improve operational efficiency and network performance, and this will have a direct bearing on costs. Automation, cloudification, and Artificial Intelligence are essential attributes for increasing agility, thus enabling a faster rollout of services and a better customer experience.
Conclusion
-
Telco cloud environment will be intricate and heterogeneous, including multiple tiers, technologies, deployment models, applications/network functions, and APIs. The diversity of cloud computing models poses a security risk where different types of attacks are now targeting the cloud infrastructure
Security must be anintegral part of the telco cloud and the services that run on it. It needs to move from being a disjointed bolt-on to network services to be concomitant and built-in as a part of every service that is being offered by the telco cloud.Security was too siloed into multiple technology domains in the past and this resulted in many vulnerabilities in a telco cloud environment. CSPs are now realising the importance of an integrated and holistic approach towards a secure telco cloud. Traditionally,human-originated errors dominated the root causes of various security vulnerabilities, this is relevant for telco clouds as well. These human errors can be effectively eliminated through automation.In my view, automation must become the new normal for CSPs. With 5G and edge potentially opening the network to web-scale competition, security will surely be a key characteristic in enabling CSPs to differentiate their solutions and their new network infrastructure in the 5G realm.
Weekly Brief
I agree We use cookies on this website to enhance your user experience. By clicking any link on this page you are giving your consent for us to set cookies. More info
Read Also













